Page Not Found
Sorry! The page you were looking for is no longer available or the link has expired. If you were looking for a specific product, you can search our store.
While you’re here, take a look through some of our great articles!
Goat birthing and raising kids
By Jackie Clay
Issue #112 • July/August, 2008
Dairy goats form one of the cornerstones of our homestead. Not only do they provide milk, cheese, ice...
Time to Forget About Snail and Slug Bait
By Lyle Dykes
Issue #135 • May/June, 2012
Years ago when traveling on business, I looked out of the window of my motel one morning in...
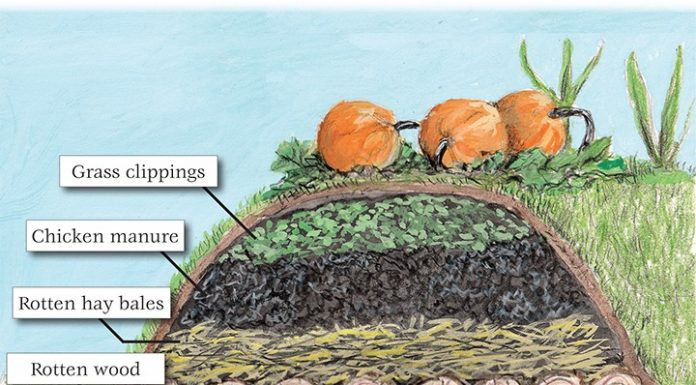
Plant Once Harvest for Years
By Jackie Clay-Atkinson
Issue #140 • March/April, 2013
Year after year we start seeds, till the ground, plant, weed, harvest, then tear it all out at...
Raised Bed Gardening — Neat and Productive
By Alice B. Yeager
Issue #74 • March/April, 2002
Are you tired of raising a big row crop gardenone that keeps you busy from dawn until...
By John Silveira
Issue #30 • November/December, 1994
(This is a four-part series. Click the links to navigate to parts one, two, three, and four.)
(When we left off last issue, O. E. MacDougal and John Silveira were travelling from Ojai, California, to Ashland, Oregon. Mac was talking about the First Ladies...
Friends and Fellow Citizens: The period for a new election of a citizen, to administer the executive government of the United States, being not far distant, and the time actually arrived, when your thoughts must be employed in designating the person who is to be clothed with that important...
By Tom Kovach
Growing up on a farm in north-central Minnesota wasn’t all chores and hard work … although there was plenty of that too. But back in the l950s and early l960s when I was growing up there were a number of small farms like ours within a mile...